- 31 Posts
- 35 Comments

 14·8 months ago
14·8 months ago

 3·8 months ago
3·8 months agoHave I been pawned is really nice, but only includes confirmed data leaks. If you use other services like Google or Malwarebyte, they will tell you more leaks. I was involved with the MoveIt data leak from a financial institution recently, which basically leaked all the information that possibly can be partly/wholely used for identity theft. This didn’t show up in HIBP. Fidelity Financial Life Insurance just leaked enough info via Infosys for another 30,000 customers with enough data for identity thefts recently.
In the US, it seems if somebody is able financially to aggregate all these sensitive data leaks, they probably can cause havocs to many people. These info often come from financial institutions, which you can’t totally withhold or lie about your personal information.

 81·8 months ago
81·8 months agoSpoofing a number means they can call somebody and appears as calling from your number. In order to receive SMS or call made to your number, they would have to hijack your SIM, typically convincing your telecom provider to transfer your phone info over to theirs.
In the US, someone knowing your full name and phone number is commonplace. There is no wide-spead havoc because of this. Someone who wants to harm you would really have to be motivated to get more information from the info you gave them. This is obviously possible because of wide-spread data leaks, but does your emissary have the perseverance and the knowledge to do this?

 51·8 months ago
51·8 months agoI am somewhat reluctant to say it, but if you get into a top-branded school, it will absolutely help you as it will open doors that otherwise would be closed. People will look at you differently, expect from your differently, and you’ll expect from yourself differently.
OTH, look at Bill Gate, Steve Job, Michael Dell, etc.; extraordinary people will be extraordinary given the right circumstances, ideas, and perseverance.

 41·8 months ago
41·8 months agoThe MLs have been shown to be extraordinarily good at statistically guessing your words. The words covered are probably comprehensive.

 151·9 months ago
151·9 months agoA speculation, https://www.phoronix.com/news/HDMI-2.1-OSS-Rejected, about HDCP, i.e. not exposing technical details as to prevent video copying, was offered.

 2·9 months ago
2·9 months agoboth
Town-square when they lure you in, they own everything when they sell you ass off.

 3·9 months ago
3·9 months agoYeah, the app data are separated and inaccessible, unless specified by the developer. Accessibility service is a separate permission, and should almost never be asked or granted, where as file/photo accesses are more common.

 11·9 months ago
11·9 months agoI agree with you. The article give a good warning about downloading applications in general, but hand-wave how they escalated from “file/photo” access to capturing your data. The recent Anatsa malware’s details seem to imply accessibility service. This is a Thread Fabric article about Anatsa malware: https://www.threatfabric.com/blogs/anatsa-trojan-returns-targeting-europe-and-expanding-its-reach

 5·9 months ago
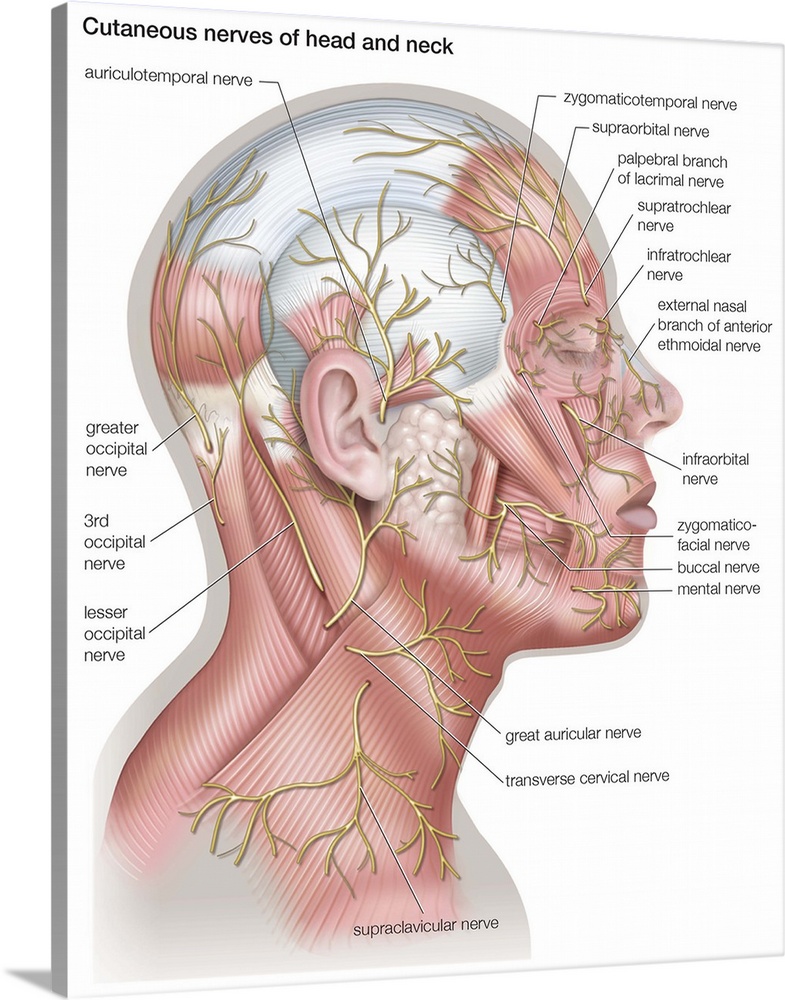
5·9 months agoFrom the project’s page:
The wearable system captures peripheral neural signals when internal speech articulators are volitionally and neurologically activated, during a user’s internal articulation of words.
It doesn’t capture the central signal, but peripheral, most likely from the nerves running around your face and your neck used to produce speech.

 8·9 months ago
8·9 months agoNo dirty thoughts! No dirty thoughts!

 6·9 months ago
6·9 months agoNo, it appears to be an external headset, although it was noted that people wearing it looked like they had head injuries, but they are working on improving it so that it is less visible.

 1·9 months ago
1·9 months agoThe article claims that the default assistant for a new phone is Gemini, but it seems people who responded here haven’t seen it. I already have the option to switch to Gemini, which I haven’t.

 2·9 months ago
2·9 months agoLovely, that’s a trick I haven’t tried on Andorid.

 4·9 months ago
4·9 months agoGoogle assistant “app”: https://play.google.com/store/apps/details?id=com.google.android.apps.googleassistant&hl=en&gl=US
I think once it’s rolled out in your region, the assistant will pester you to switch to Gemini.
There is no Gemini app of any kind for me either.

 9·9 months ago
9·9 months agoIt looks like you can switch the assistant to the old one, and then turn that one off.
But just like Microsoft, Google is going to use this technology everywhere. If in the future (or now, if it is already available to you), you use features to describe images, summarize data, create texts, you probably will be using some form of Gemini.

 1·9 months ago
1·9 months agoConsidered it done. ;-)

 1·9 months ago
1·9 months agoThe CVE-2023-52160, which applies to Android/linux/ChromeOS devices connecting to WPA2/WPA3 Enterprise, allows an attacker to fool the user to connect to a malicious SSID and intercept the traffic. So unencrypted traffic can be compromised. So, their listing of sensitive data, BEC, and password theft sound scary but probably affects very few services that don’t encrypt the data.

 9·9 months ago
9·9 months agoYeah, check out this link: https://www.top10vpn.com/research/wifi-vulnerabilities/ , it says any Linux device running Intel’s iNet Wireless Daemon in an AP mode.

 9·9 months ago
9·9 months agoAI is most likely here to stay, so if you have it do “good” things effectively, then’s it’s a good boi. If it is ineffective or you have it do “bad” things, then it’s a bad boy.